From SSRF to RCE: A 7-Step Chain Against PostHog
A deep dive into how overlooked validations, a SQL escaping bug, and static credentials turned a simple webhook into a full system compromise.
When a 24-hour research window turned into a 7-step RCE chain, we found that PostHog’s SSRF, a ClickHouse 0day, and default PostgreSQL credentials were the perfect storm for a full remote code execution.
A deep dive into how overlooked validations, a SQL escaping bug, and static credentials turned a simple webhook into a full system compromise.
Source: Mehmet Ince @mdisec — Source link
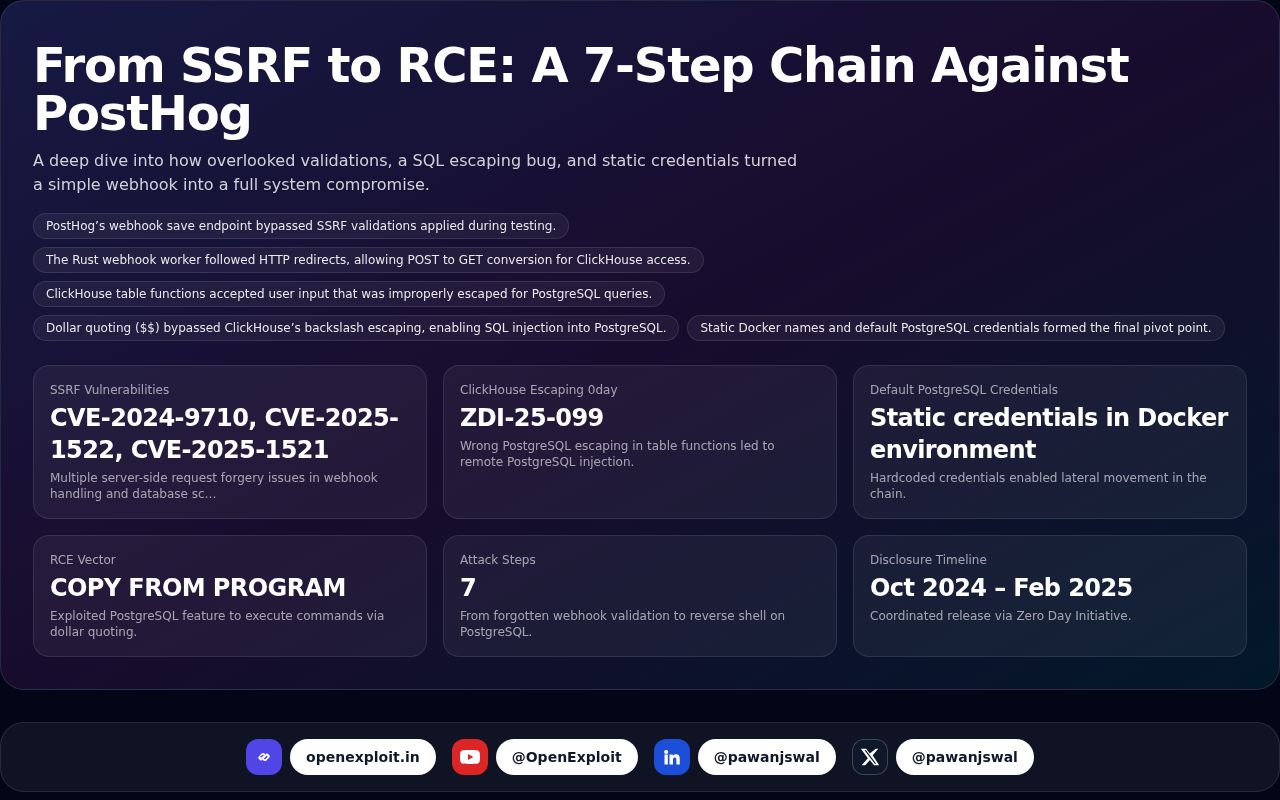
Highlights
| Metric | Value | Notes |
|---|---|---|
| SSRF Vulnerabilities | CVE-2024-9710, CVE-2025-1522, CVE-2025-1521 | Multiple server-side request forgery issues in webhook handling and database schema. |
| ClickHouse Escaping 0day | ZDI-25-099 | Wrong PostgreSQL escaping in table functions led to remote PostgreSQL injection. |
| Default PostgreSQL Credentials | Static credentials in Docker environment | Hardcoded credentials enabled lateral movement in the chain. |
| RCE Vector | COPY FROM PROGRAM | Exploited PostgreSQL feature to execute commands via dollar quoting. |
| Attack Steps | 7 | From forgotten webhook validation to reverse shell on PostgreSQL. |
| Disclosure Timeline | Oct 2024 – Feb 2025 | Coordinated release via Zero Day Initiative. |
Key points
- PostHog’s webhook save endpoint bypassed SSRF validations applied during testing.
- The Rust webhook worker followed HTTP redirects, allowing POST to GET conversion for ClickHouse access.
- ClickHouse table functions accepted user input that was improperly escaped for PostgreSQL queries.
- Dollar quoting ($$) bypassed ClickHouse’s backslash escaping, enabling SQL injection into PostgreSQL.
- Static Docker names and default PostgreSQL credentials formed the final pivot point.
- The chain culminated in a reverse shell via COPY FROM PROGRAM on the PostgreSQL instance.
Timeline
- 2024-10-03 — Vulnerability reported to vendor by ZDI
- 2025-02-25 — Coordinated public release of advisory
- 2025-02-25 — Advisory updated
Why This Matters
This chain demonstrates how modern microservice architectures can amplify the impact of seemingly low-severity issues when combined. It underscores the importance of consistent input validation, secure defaults, and defense-in-depth for distributed systems.